Since Hightouch manages the flow of your business-critical data, we provide a full suite of platform governance features to ensure security and compliance. These features fall into two categories: access management and change management.
Before going in-depth on these features, it's helpful to understand the core concepts Hightouch uses to structure workspace management features.
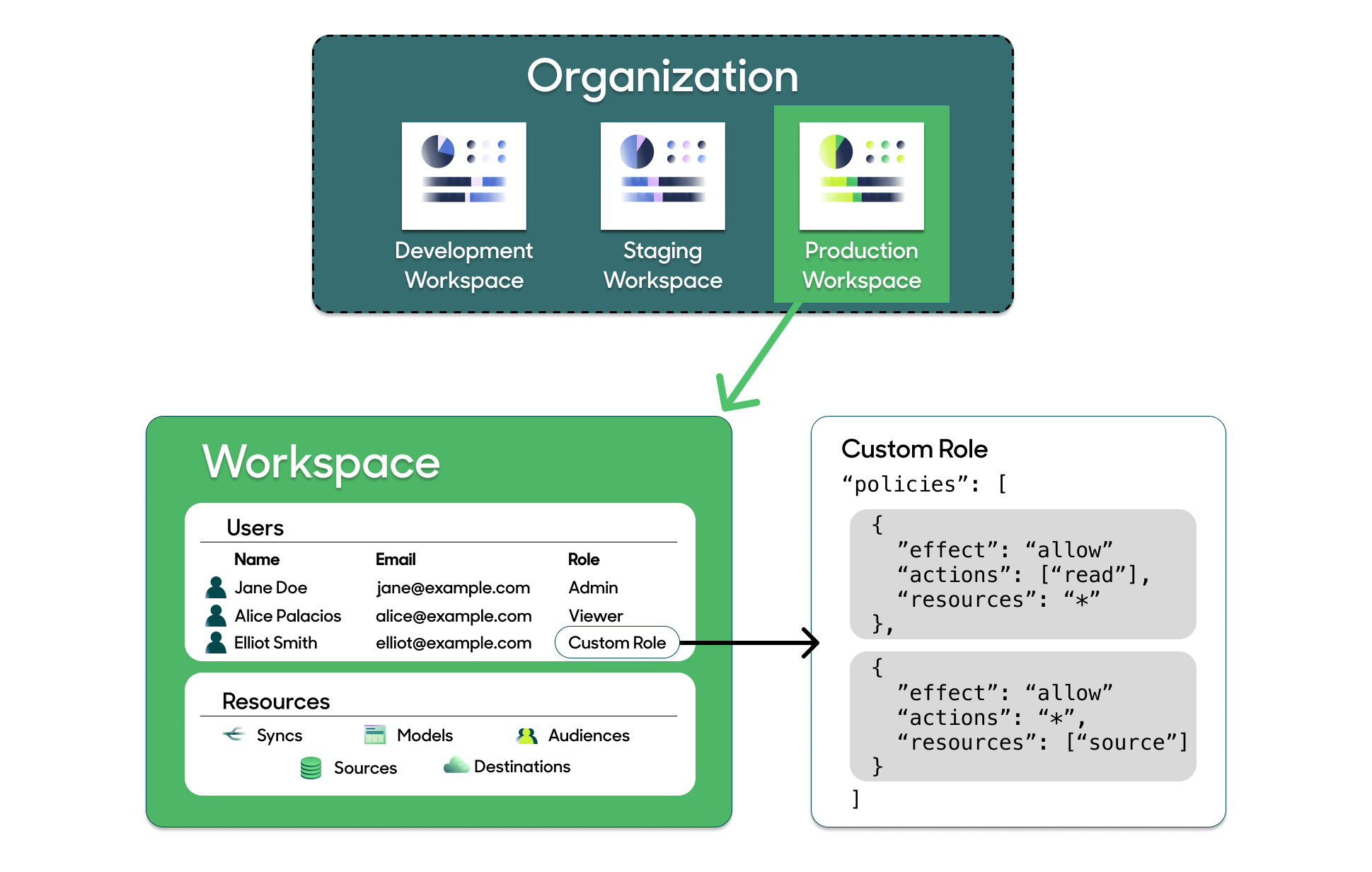
Core concepts
- Organization: a container for a set of workspaces, used for billing purposes.
- Workspace: a Hightouch account representing a set of resources and users. All settings apply at the workspace level, except for SSO, which applies at the organization level.
- Environment: a Hightouch workspace you've designated for development, staging, or production purposes.
- User: an individual with access to a workspace. A user can be associated with one or more workspaces.
- Role: a set of policies governing a user's access to resources. Users can only be assigned one role.
- Policy: a set of actions users can take on resources given certain conditions.
- Resource: any of the building blocks of a workspace: for example, sources, destinations, models, syncs, and audiences.
- Linked resources: Resources of the same type, for example, sources, that are linked across environments.
When you have many resources in the same workspace, it can be helpful to organize and navigate them using folders and filters.
Access management
Hightouch's access management features let you govern who can access your workspaces and what actions they can take.
Access management features include:
- SAML single sign-on (SSO) to support organizational access and user creation
- Role-based access controls (RBAC) to govern and customize what actions users can take
- SSO groups to support workspace and role assignment at scale
- Label-based access controls (LBAC) to provide deeper access granularity
Invite team members
You can choose to invite team members to your workspace manually or enable access for your entire organization using SAML SSO. Before inviting team members, you may want to change the default role for a workspace or set up SSO groups to map groups in your identity provider to Hightouch roles.
To manually invite a team member, go to the Members tab on the Settings page and click Invite new people.
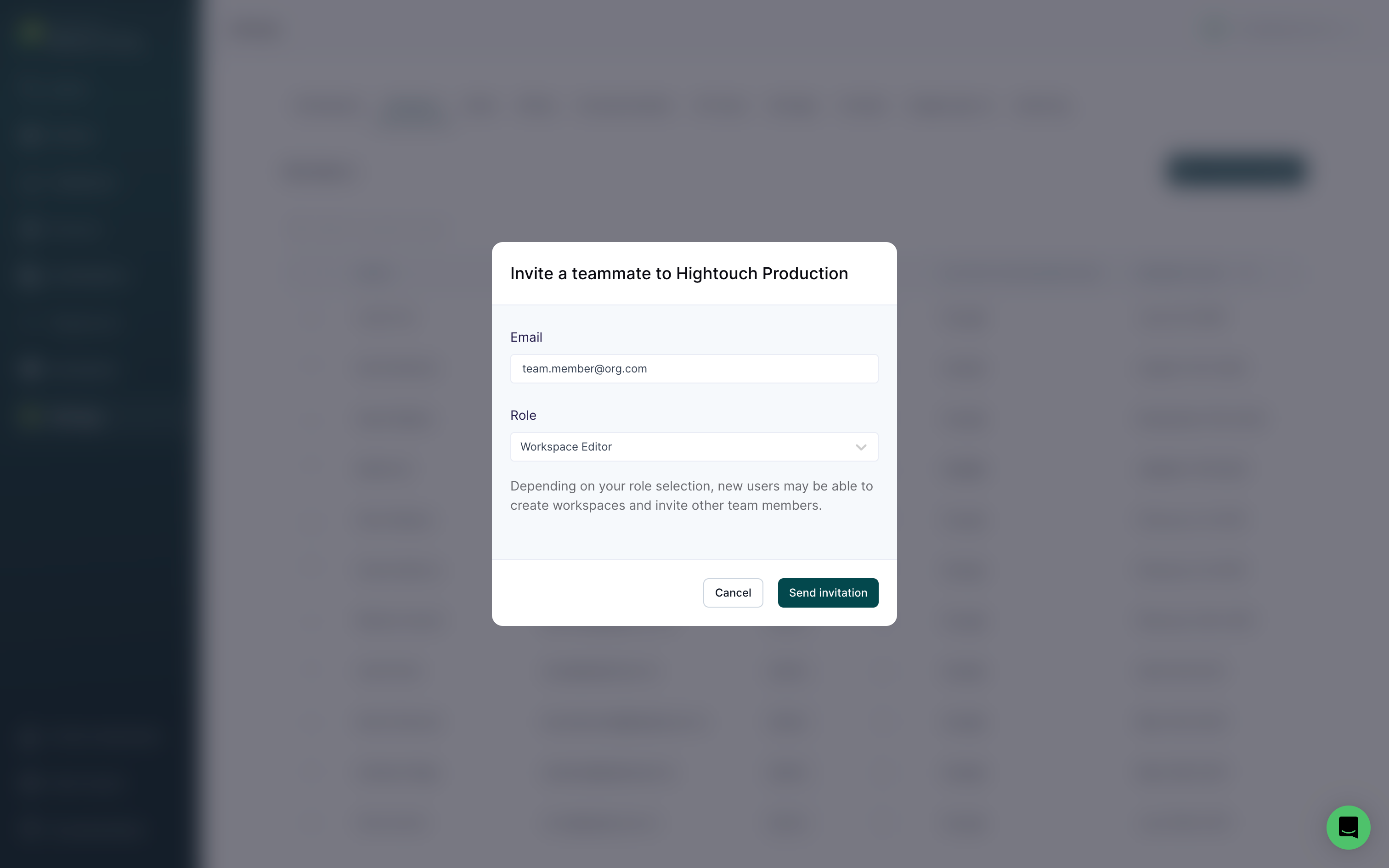
In the modal that appears, enter your team member's Email, select the appropriate Role, and click Send invitation.
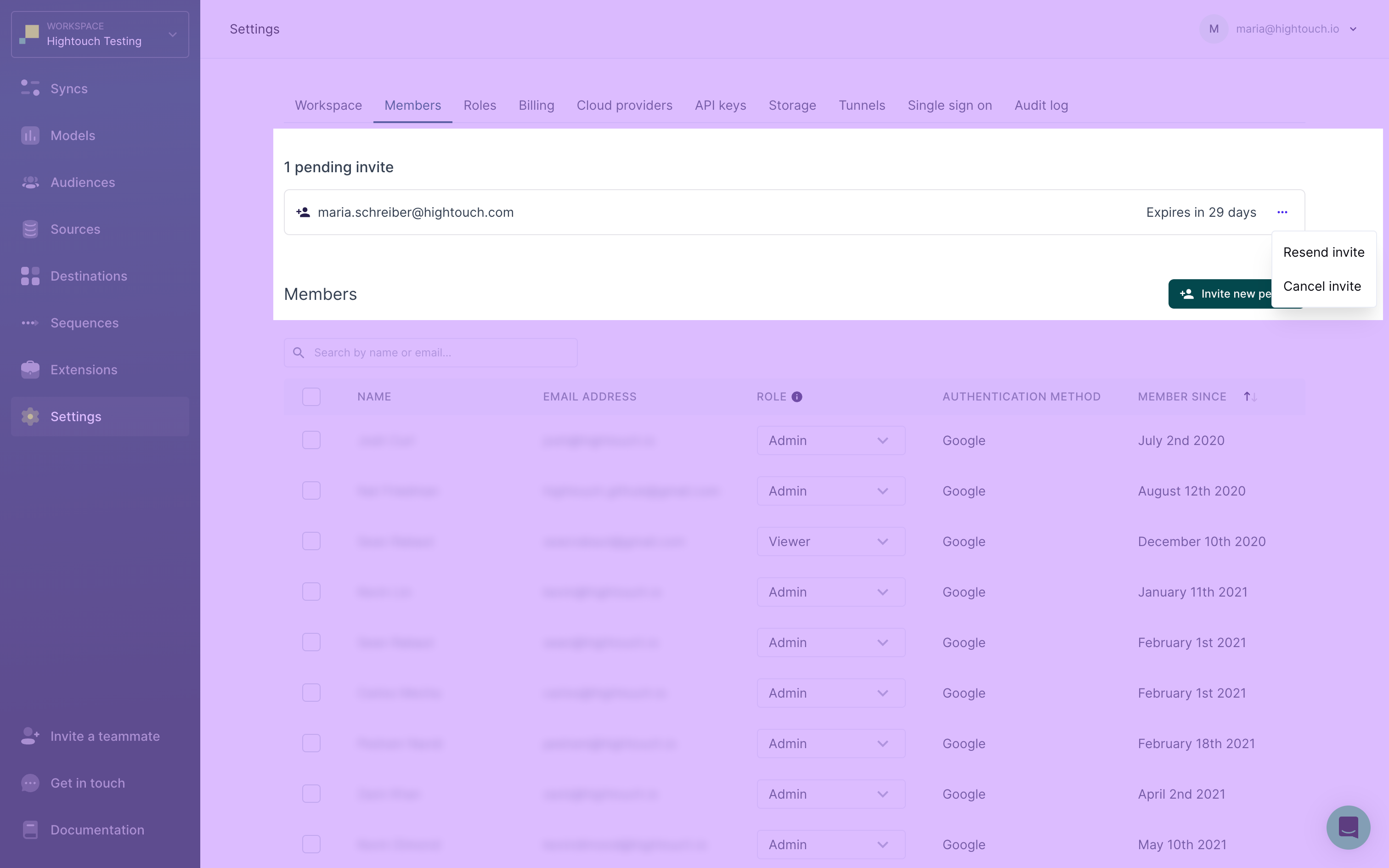
The Members tab displays pending invitations and team members. You can choose to resend or cancel any pending invitations. Outstanding invitations are active for 30 days.
Check out the SSO documentation to learn how to configure SAML SSO to provide access for your entire organization through an identity provider like Okta or Azure Active Directory.
Accept an invitation
Once you receive the invitation to join your team's Hightouch workspace, click the Join workspace button in the email to access the Log in to Hightouch page.
Select the correct login method based on the credentials you would like to use to access the workspace. A wrong selection can cause an Invalid invitation error.
If you see this error even after selecting the correct login method, we recommend logging in using an incognito browser tab. This can help avoid issues with your browser cookies interrupting the correct login flow.
If your email address is associated with a Google Account, click Log in with Google. Enter your Google Account credentials to proceed.
If your email address is associated with a Microsoft Account, click Log in with Microsoft. Enter your Microsoft Account credentials to proceed with logging in.
If your organization set up Single Sign-on, you don't need to receive and accept an invitation to join your Hightouch workspace. As described in the SSO FAQ section, you can join your workspace directly by accessing the Login URL displayed on the Single sign-on tab of your company's Hightouch workspace.
Otherwise, you can click Log in with SSO and insert your company's Organization identifier.
After successfully logging in, you appear as a new member on your Hightouch workspace's Members tab.
You only need to accept an invitation once. To access your Hightouch workspace in the future, go to the generic workspace access page. If your login credentials are cached in your browser, you will be redirected to your Hightouch workspace. Otherwise, you will be redirected to the login page.
When logging in, make sure to always select the same login method that you chose when logging in for the first time. This prevents creating duplicate users.
Remove team members
To remove team members, go to the Members tab on the Settings page and check the boxes next to the members or members you would like to remove. Then click Delete selected members at the top of the page and confirm your choice in the popup window.
If you remove a workspace member, all resources they created, such as models and syncs, will continue to exist — You don't need to migrate them to a different member.
However, it's best to reauthorize any source or destination configurations that use a removed member's credentials. By reauthorizing them with a current member's credentials, you can avoid a credential's expiration interrupting your syncs.
If possible, use service accounts to authorize connections with resources rather than individuals' user accounts.
Default role settings
Unless you've setup SSO group mappings to Hightouch roles, Hightouch assigns new members the default workspace role.
You can change the default role for a workspace from the Workspace tab on the Settings page. Select the appropriate role for users from the dropdown under the Default role header.
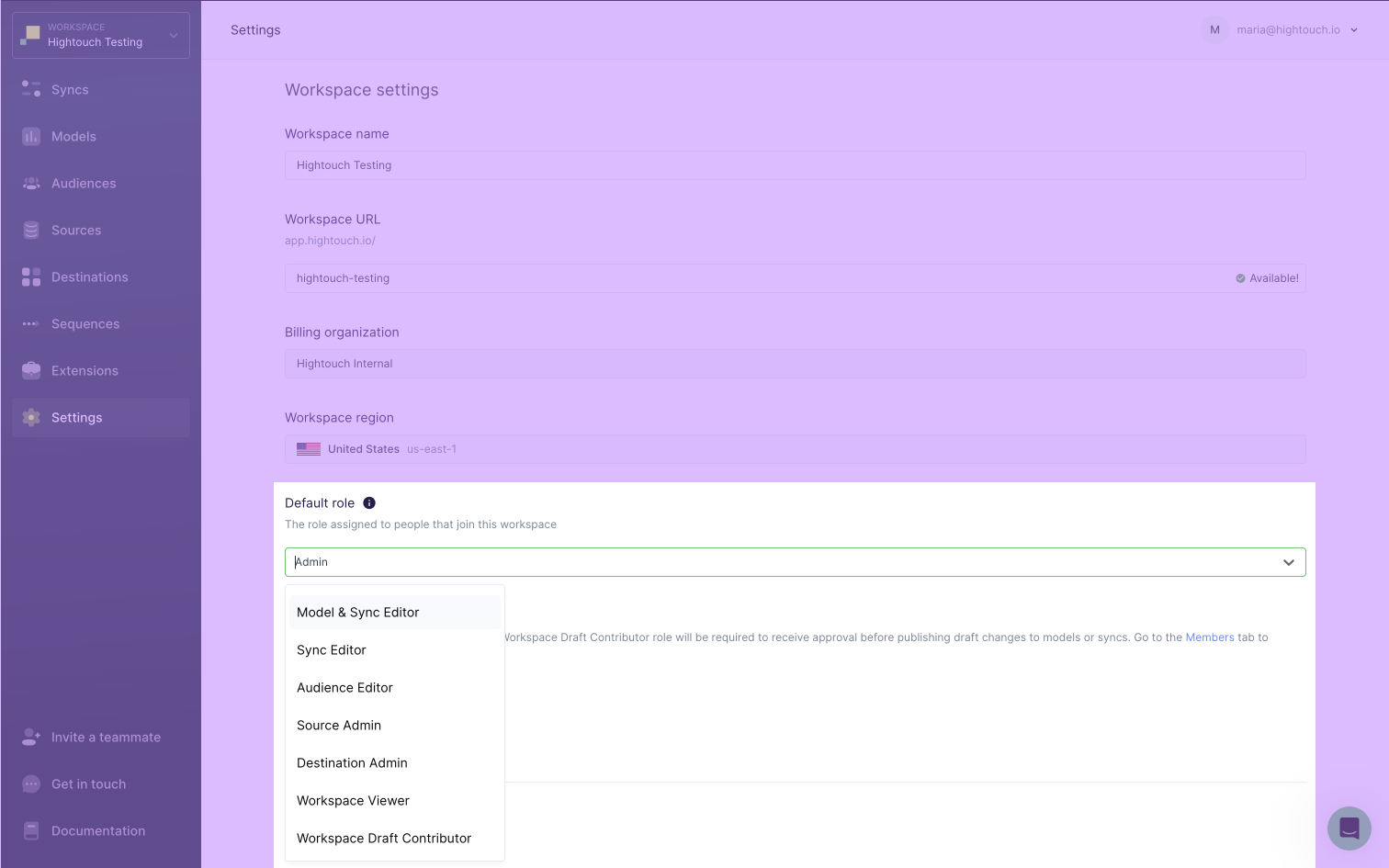
Be careful when downgrading the default role, for example from Admin to Viewer. You may be unintentionally stripping users of permissions. Review role definitions before setting the default role to select the appropriate role for your workspace.
From the Workspace tab, you can also toggle off using the default role for SSO users.
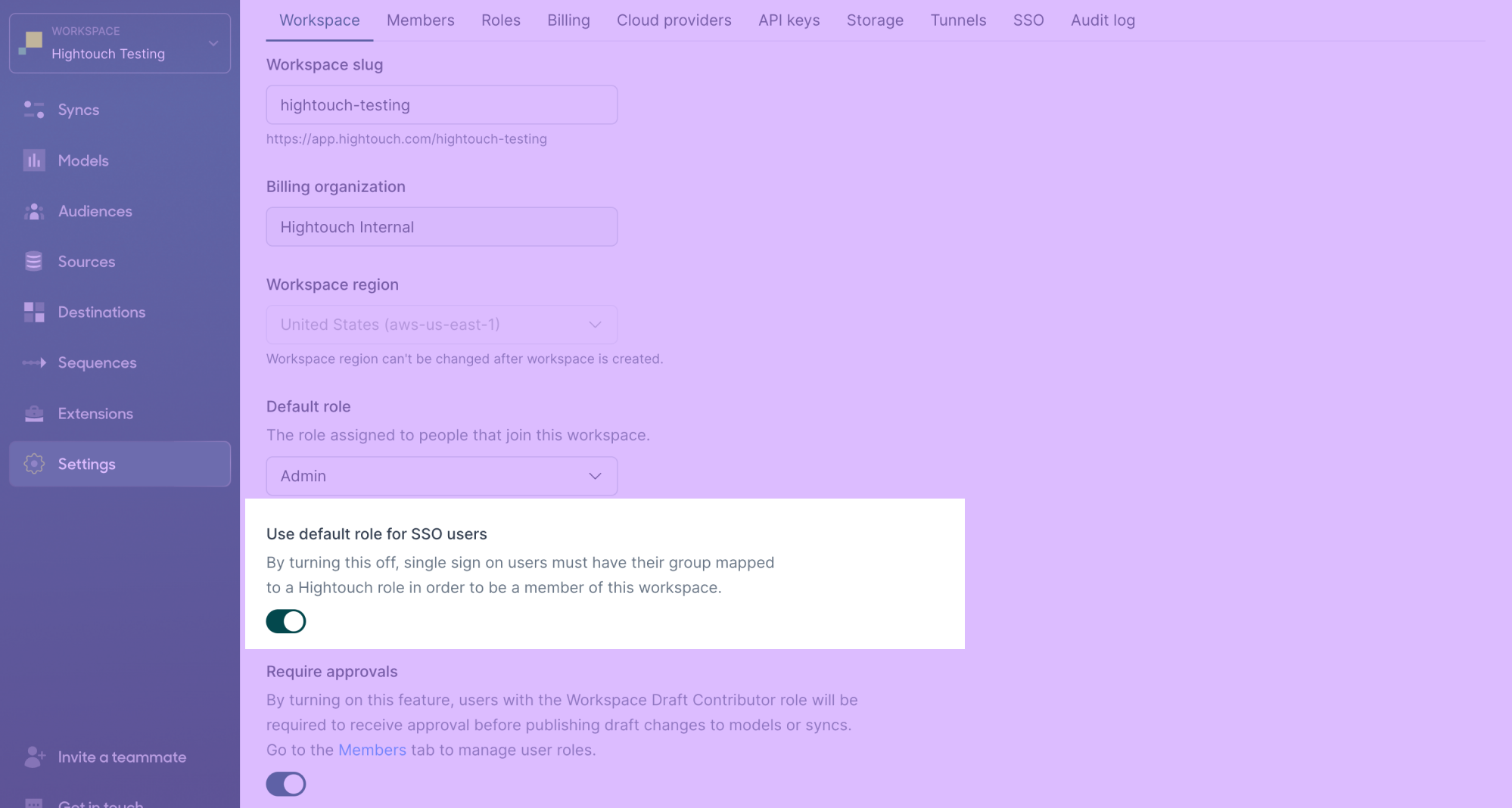
Your organization may want to do this to restrict unintended access to your workspace. By toggling this setting off, users won't have access to workspaces that have enabled SAML SSO unless they belong to an identity provider group that has been mapped to a Hightouch role.
Change user roles
Unless you've setup SSO group mappings to Hightouch roles, you can change an individual user's role from the Members tab on the Settings page. This page displays a table of all users in your workspace.
Each user row has a Role dropdown where you can select that user's role. You can create custom roles for assignment using role-based access controls.
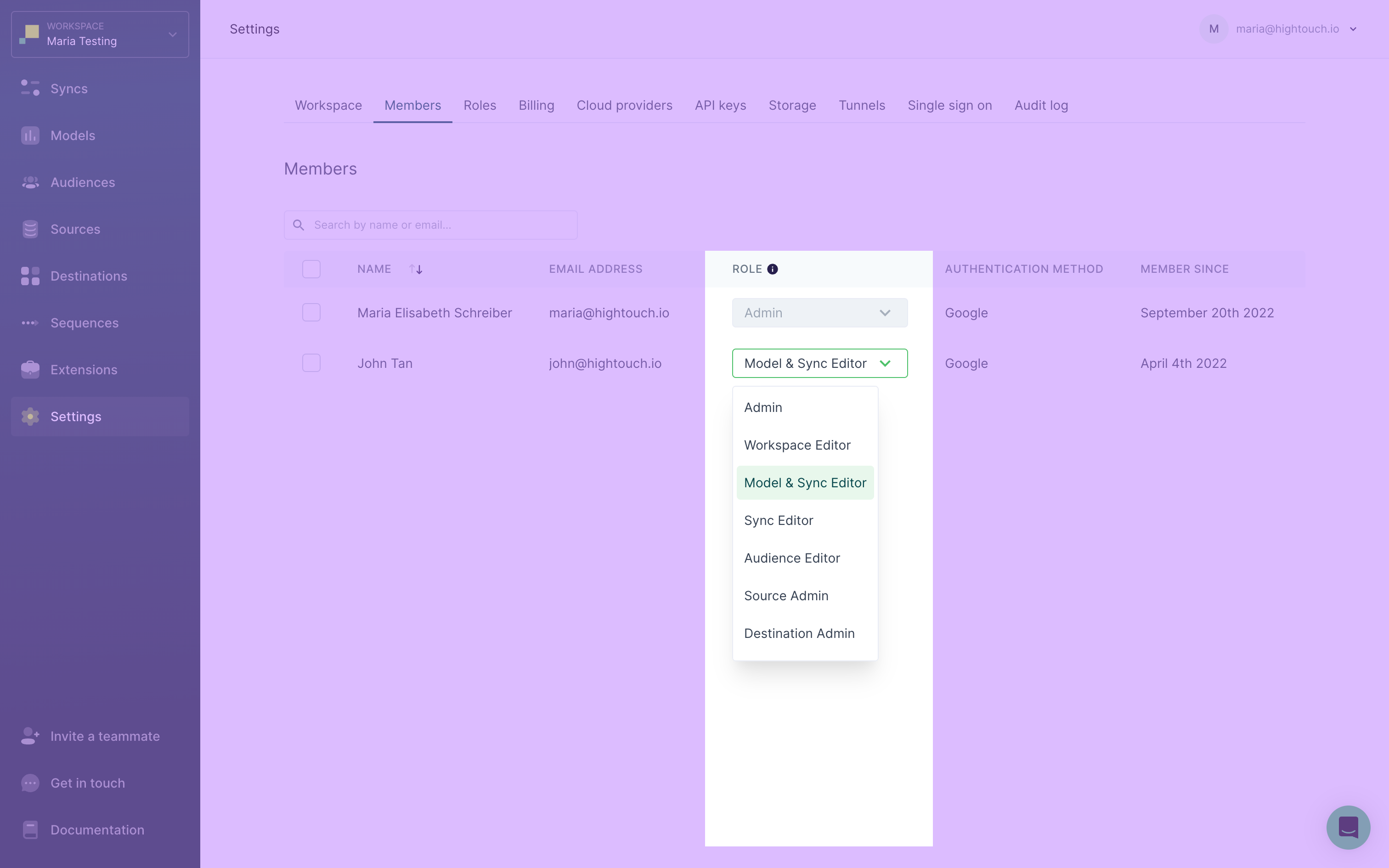
Changing individual user roles isn't allowed for workspaces using SSO since we don't want to enable users to circumvent permissions set in their organization's identity provider.
Check out the SSO groups documentation to learn how to automatically assign roles to team members based on their group in your identity provider.
Workspace authorization
Workspace authorization settings determine the visibility and access to workspaces in your organization. You can find Workspace authorization settings in the Workspace settings tab.
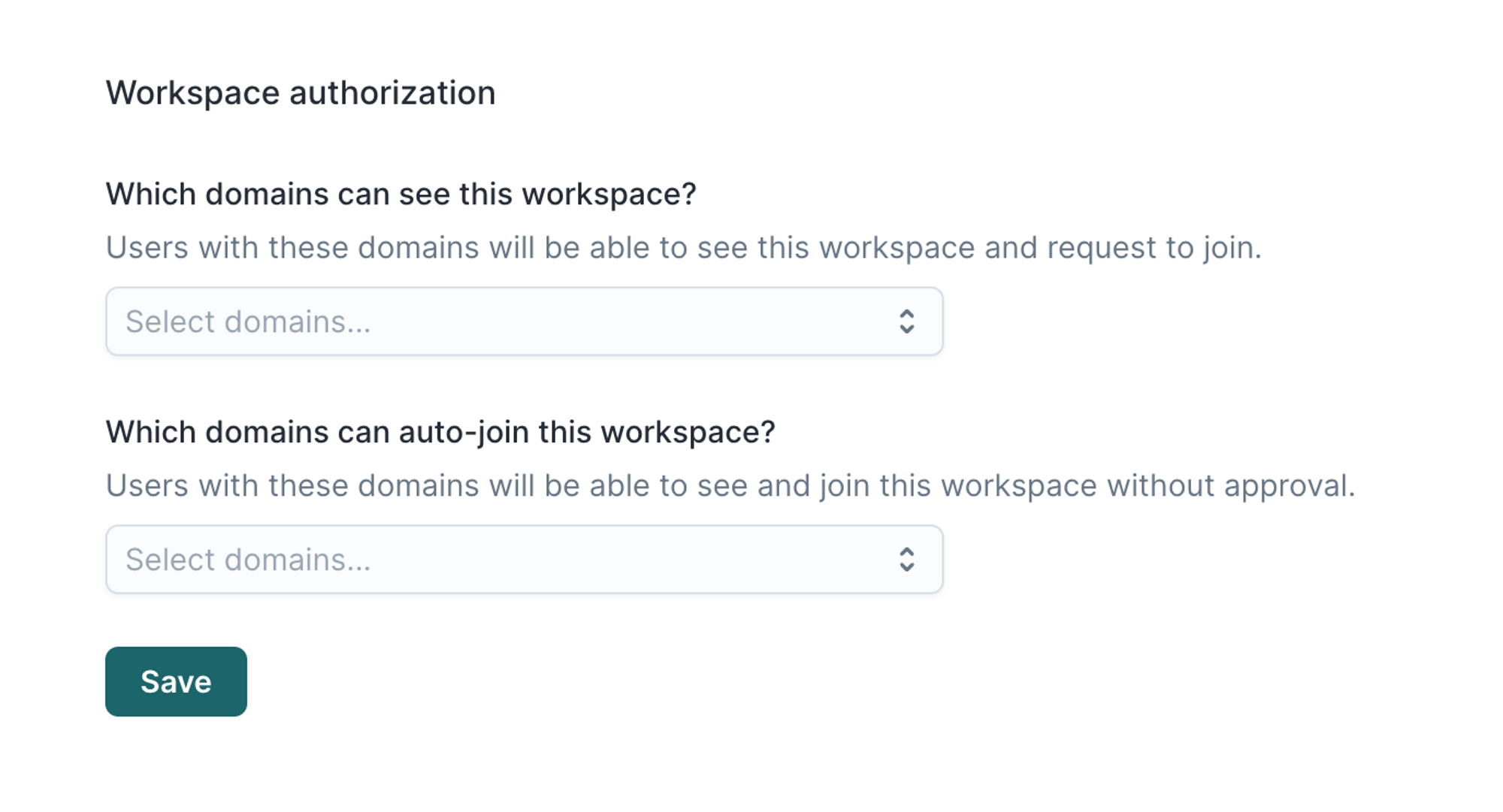
The first setting, Which domains can see this workspace?, determines the workspace's visibility. Hightouch displays the workspace on your organization's workspaces page for any domains you've configured.
The second setting, Which domains can auto-join this workspace?, determines whether the workspace displays a Join or Request access button if a user with a particular domain isn't a member.
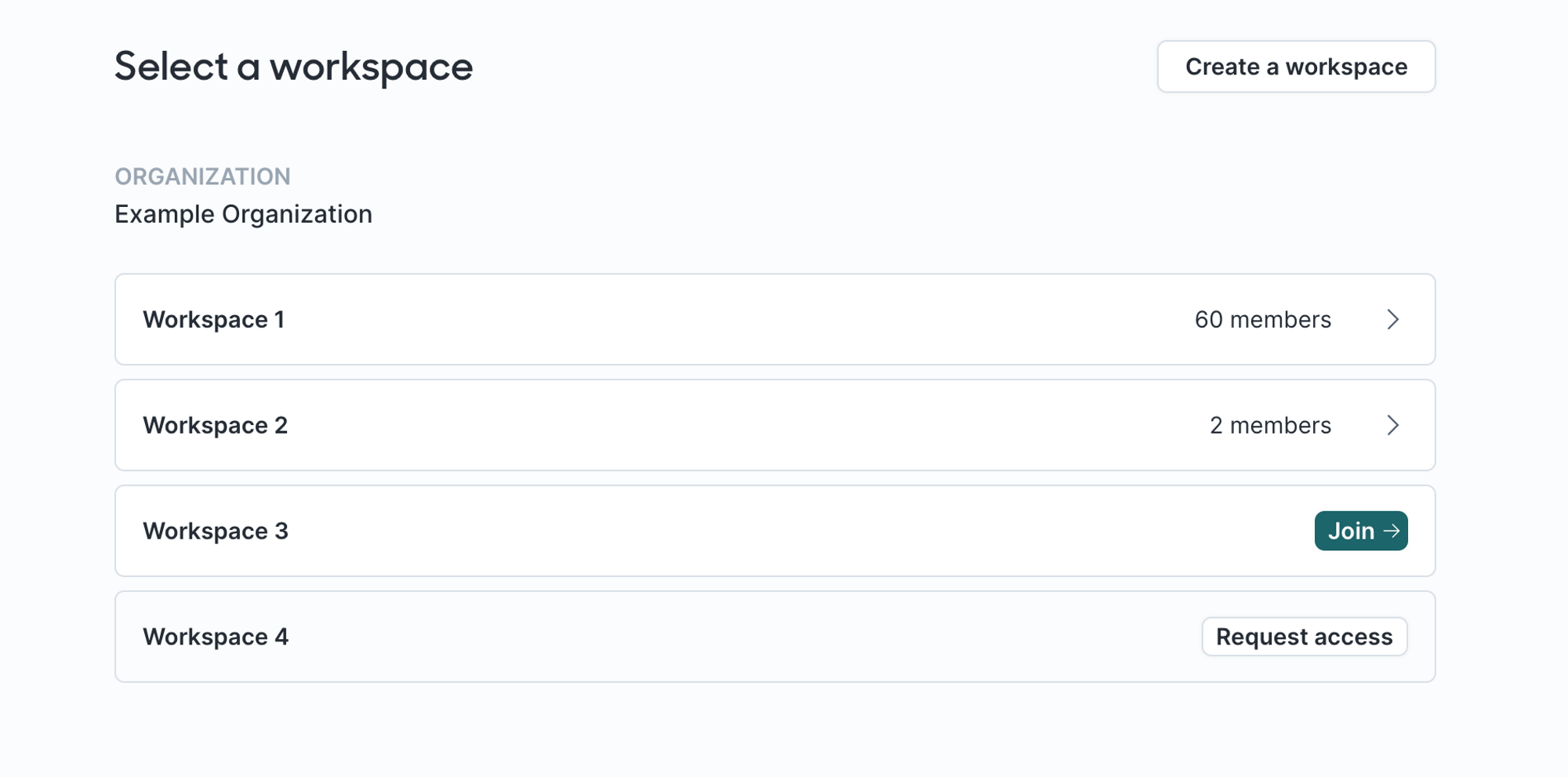
If a user can join a workspace without approval, they can see a Join button. After clicking it, they're automatically added as a new member to the workspace.
Otherwise, they must click the Request access button. This request appears in the Awaiting approval section of the Members tab and must be approved by a current member of the workspace by clicking Approve access.
Change management
Hightouch's change management features let you enforce reviews of changes and allow you to view historical in-app changes.
Change management features include:
- Approval flows to stage changes before pushing them into production
- Environments to maintain separate workspaces and deploy changes to linked resources
- Audit logs to provide records of what changes were made, by whom, and when
Use approval flows
Approval flows make it so that any changes made by users with the Workspace Draft Contributor role require approval from a privileged user. Check out the approval flows documentation to learn more.
Configure environments
You can create environments in-app to organize and link resources between environments. You can then deploy changes from one linked resource to another. Check out the environments documentation to learn more.
View audit logs
Hightouch provides audit logs to track, trace, and search through historical actions taken in the Hightouch app. Check out the audit logs documentation to learn more.